You’ve seen it happen. A new user signs up, places an order, or requests a code — but something doesn’t feel right. Maybe the phone number looks off, or the same number appears across multiple suspicious accounts. That’s where phone verification comes in. It’s your quiet, behind-the-scenes defense against fraud, bots, and wasted marketing spend.
In today’s digital world, you can’t rely on email alone to confirm identity. You need something users always keep close — their phones. A phone verification API does exactly that. It confirms people are real without ruining the signup flow, helping you build trust and security from the first tap.
Why Phone Verification API Matters Right Now
You care about growth that sticks. You also care about clean user authentication that protects your brand and time.
The Rising Cost Of Fake Accounts
Fake signups drain support and inflate CAC. Bad actors test stolen cards through low-risk transactions. They recycle the same mobile phone number across throwaway profiles and exploit international phone numbers to hide patterns. You pay in refunds, chargebacks, and wasted outreach. The phone number provided becomes a weak link if you never verify it. Strong checks create cost savings you can measure.
Phone Numbers As A High-Signal Identity Anchor
A verified number ties activity to a durable identifier. It is harder to fake than email and follows the user across devices. That stability helps you see real customers and improves conversion rates across your app and funnel.
The UX And Revenue Angle You Can’t Ignore
Good sessions should feel smooth. Place verification where risk is highest and keep it fast. You prevent fraud without scaring off honest businesses during registration or later communication by SMS. The payoff is cleaner cohorts and fewer headaches for your team.
How Phone Number Verification APIs Actually Work Under The Hood

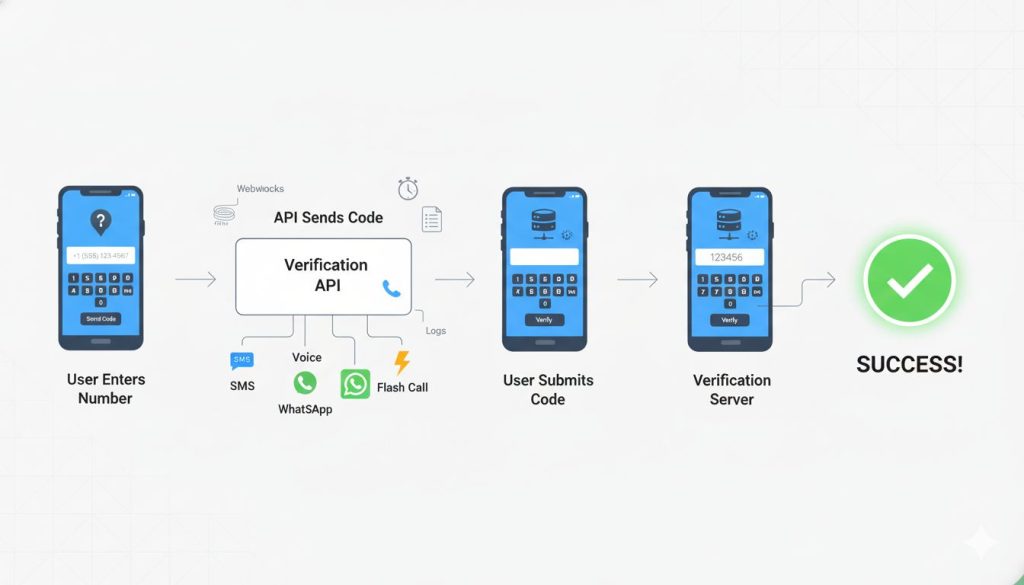
You want a clear picture of the workflow from the first tap to a confirmed code. Here is the lifecycle you can build and monitor.
From Request To Code: The Verification Lifecycle
Your app sends an API request to the number verification API. The service generates a code, hashes it, and selects a channel. It sends the message and binds the attempt to the session. The user enters the code. You check the hash, mark success, expire the record, and log outcomes. You also track requests volume and undelivered messages to tune reliability.
Channels Explained: SMS, Voice, Flash Call, And WhatsApp
Use multiple channels to fit user preferences and country rules. SMS is familiar and quick. Voice helps when SMS filters are strict. Flash call can be fast in selective regions. WhatsApp is strong where the app is common. A lookup API can support phone number validation and carrier detection before you send. That reduces waste and improves deliverability.
Anti-Abuse Add-Ons That Make A Difference
Enable line type detection to limit VOIP abuse. Capture device, IP, and network signals in real time. The verify API returns a validation result you can act on inside a single API flow. Document retries and webhooks in clear HTTPS documentation. Service health matters, so note error codes and timeouts. Treat monitoring as part of the method, not an afterthought.
Choosing The Right Verification Flow For Your UX
Your goal is simple. Make fraud expensive and honest use effortless.
Where To Place Verification In The Journey
Place checks where risk peaks. At signup for high-abuse products. At payout changes and password resets for financial actions. Use progressive steps. Start with soft signals on international numbers, then require a code for higher risk moves. Respect unique international dial codes and local rules when you verify across countries.
Code Length, Timeout, And Retries That Don’t Annoy
Use 4 to 6 digits with a TTL between 60 and 120 seconds. Offer voice fallback for roaming users. Align national numbers and international formats in your forms. Detect line type so you treat landlines and mobiles correctly. Map phone number type to routing rules. Keep number validation fast and transparent.
Handling International Numbers And Other Edge Cases
Show the country picker with location data when helpful, but never expose full location information. Handle dual-SIM, weak network, and offline states gracefully. Optimize copy for screen readers. Verify without blocking access to the rest of the process when safe. Localize for America and other regions. Aim for quality communication that helps the end user complete identification with minimal friction.
Guardrails, Compliance, And User Trust
You operate in regulated rails. Get consent right, follow messaging rules, and tell users what you are doing. That balance builds trust and keeps deliverability high.
Consent, Messaging Policies, And Carrier Rules
Use clear opt-in language at signup and in-product. Honor country-specific policies. Understand A2P and 10DLC basics in the US, and register templates where required. Respect quiet hours and frequency limits. Keep unsubscribe flows simple.
Privacy By Design
Collect only what you need. Hash codes and encrypt logs at rest. Set short retention windows, with clear deletion paths. Keep data in-region when laws require it. Limit internal access through roles and audit trails.
Transparent UX That Builds Confidence
Explain why you verify and how often you might contact the user. Show what you store and for how long. Provide an easy way to stop messages or change numbers. Use plain language, short screens, and predictable timing. Close the loop with a success state. Publish a contact path for questions. Link your policy from every relevant screen.
Integration Game Plan: From Sandbox To Production
You want a rollout that is boring in the best way. Build a small, sharp integration in the sandbox, then harden it before you flip traffic.
Design Your Verification Abstraction
Wrap your provider behind a clean interface. Expose simple send and verify methods, with a stable request and response shape. Centralize error handling and translate vendor errors into app-safe codes. Keep business rules out of controllers.
Webhooks, Idempotency, And Retries Done Right
Accept webhooks for delivery and status changes. Make endpoints idempotent using tokens or event IDs. Store verification state atomically so duplicates cannot corrupt it. Retry outbound calls with exponential backoff. Guard against out-of-order events with version checks.
Observability From Day One
Log every attempt with a trace ID from client to provider. Track sends, deliveries, conversions, latency, and cost per verified user. Build dashboards and weekly views. Alert on spikes in failures, timeouts, or unusual country mixes. Sample user sessions to replay flows in staging with production-like data for accuracy.
Fallbacks And Circuit Breakers
Plan for failure. Add automatic channel failover when SMS is slow. Add provider failover behind a feature flag. Use timeouts and circuit breakers to protect your app. Degrade gracefully by deferring verification when risk is low, and queue work for retry.
Measuring ROI And Success Without Guesswork
You cannot manage what you do not measure. Define a small set of metrics, review them often, and tie them to actions.
KPIs That Tell The Truth
Watch verification conversion rate across countries and devices. Track fraud incident rate, CAC savings, and refund volume. Monitor support tickets related to codes, delivery, and resets. Set weekly targets and annotate changes.
Experimentation You Can Trust
Run A and B tests on placement, channel, and TTL. Segment by country, carrier, device, and risk score. Keep guardrails for drop-off, latency, and cost per verified user. Ship small, analyze fast, then lock in gains.
Cost Control Without Cutting Corners
Blend channels by region based on delivery and price. Use dynamic routing to avoid weak routes. Block known abuse ranges and throttle noisy patterns. Reinvest savings into quality, support, and fraud tooling. Close the loop with a monthly review and a single owner.
Common Pitfalls And How To Avoid Them
Everyone makes the same mistakes at first. You can skip them with a few practical habits.
Using Verify API Too Early (Or Too Late)
Match the moment to risk. High-abuse apps can challenge at signup. Low-risk apps can wait until checkout or the first sensitive action. Do not force codes before a user sees value. Do not skip checks on password reset or payout changes.
Ignoring Local Nuances
Delivery lives and dies on local rules. Register sender IDs where required. Follow DLT and 10DLC processes. Translate templates and respect quiet hours. Test with local numbers and real handsets, not only simulators.
Treating Verification As “Set And Forget”
Threats evolve. Rotate templates, review routing, and update allow and block lists. Track carrier filters and fraud tactics. Schedule quarterly audits.
Over-Collecting Or Under-Securing Data
Store hashes, never raw codes. Mask phone numbers in logs. Use least privilege, short retention. Encrypt at rest, in transit. Prove it with access reviews and alerts.
The Bottom Line
Strong phone verification isn’t just a security layer—it’s a growth enabler. When done right, it filters out fake users, keeps real customers safe, and makes every transaction smoother. You reduce fraud, protect your brand, and save time for the work that truly matters.
Keep your approach practical. Choose the right verification channel per region, measure results, and refine with real data. Each iteration makes your flow stronger and simpler for users.
If you’re ready to explore these best practices with ease, our phone verification API integrates quickly and delivers clear metrics—ready when you are. Try our phone verification api service today!