Verifying an email address sounds simple, but anyone who’s ever managed a contact list knows how tricky it can get. One wrong character, and your message never reaches the inbox. When you’re running campaigns, onboarding users, or sending important updates, that’s a problem you can’t afford. The good news is, verifying an email doesn’t have to be complicated or time-consuming. Once you understand what to check—and how to do it—you can keep your list clean, your deliverability high, and your sender reputation strong. In this guide, we’ll walk through exactly how to verify if an email address is valid, step by step.
Why Email Validation Matters In Real Life
You send emails to grow revenue, build trust, and keep customers close. That only works if messages land where they should and your metrics stay clean.
Cost, Reputation, And Accuracy—What’s At Stake
Invalid addresses waste send credits and inflate processing time. They also create bounced emails that tank your bounce rate and hurt email deliverability over time. ISPs and filters watch these signals closely. High noise invites spam complaints and blocks. Bad inputs also corrupt analytics. One bogus contact can skew cohort results and mislead your team about what works.
Common Scenarios Where Validation Pays Off
You feel the pain most on high-intent forms and checkout flows where every lead matters. Critical flows like password resets and receipts must reach the inbox the first time. Large mailing lists from events, partners, or migrations hide landmines that slow campaigns. Proactive email verification in these spots protects send reputation, saves budget, and helps improve deliverability without adding friction.
Quick Visual Checks You Can Do Right Now
Before you touch servers or tools, scan for simple tells. These checks prevent obvious errors and keep forms friendly.
Spot-The-Error: Human-Readable Clues
Look for typos and transpositions like gamil.com or outlok.com. Trim stray spaces and repeated dots. Watch for suspicious formats such as no@no.com or nonsense local parts. Quick reads catch broken email address syntax and restore correct syntax fast.
Friendly UX That Prevents Bad Inputs
Help users succeed as they enter the email address. Offer inline suggestions like “Did you mean gmail.com?” Explain allowed characters with short hints, then highlight mistakes before submitting. If you collect lists from a website or export to Google Sheets, add a simple rule to check email addresses on paste. These small guardrails reduce cleanup work later and keep the growth smooth.
Technical Checks That Separate Valid From Wishful
Once the basics look clean, confirm the address at the infrastructure level. This is where you separate likely from real.
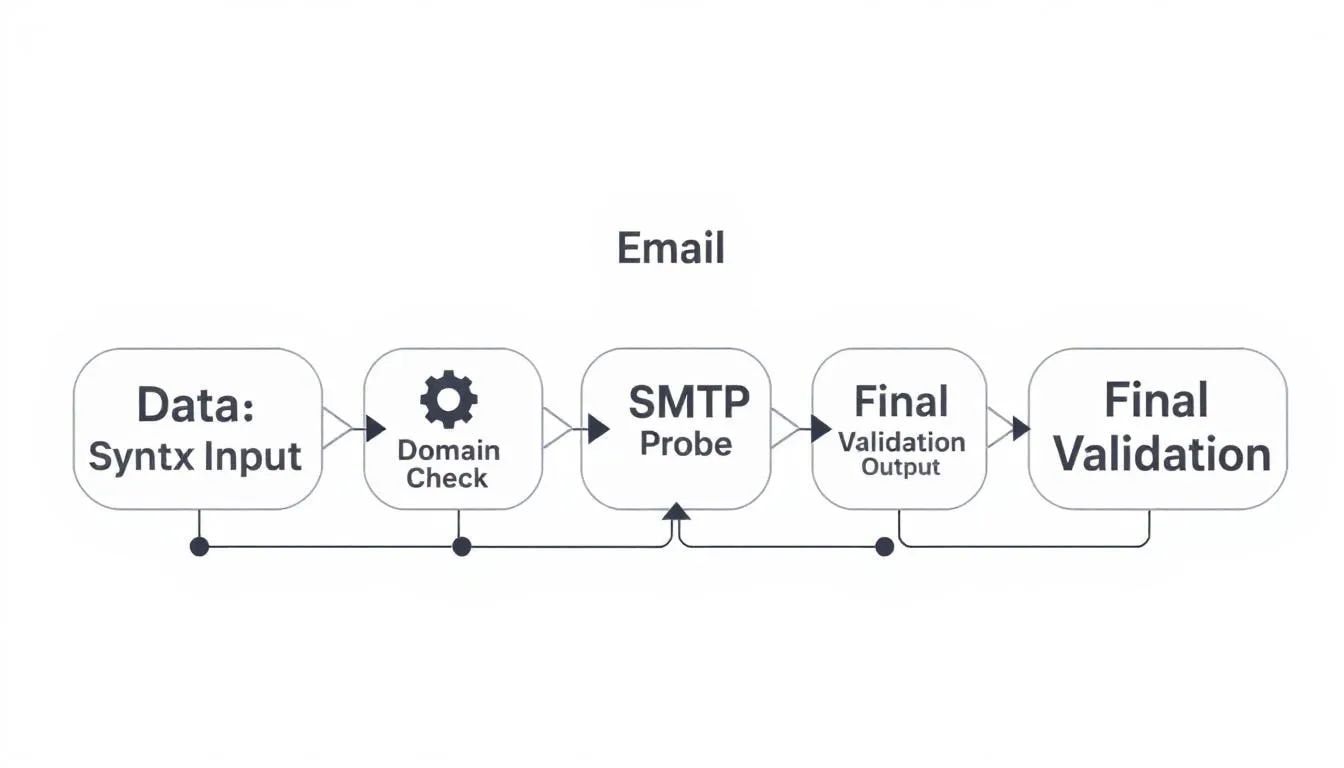
Syntax Validation That Doesn’t Overreach
Use standards-aware parsers to validate email addresses correctly. Avoid brittle one-liners. Respect Unicode local parts and internationalized domains with proper IDN handling. Good parsing sets up every later step.
Domain & DNS Reality Check
Confirm the domain exists and its DNS records resolve. Start with A or AAAA and follow CNAMEs if present. Then fetch MX records to see where the email server accepts mail. MX is a strong signal. Some domains accept mail on the root A record, but treat that as weaker evidence.
SMTP-Level Probing (Handle With Care)
If policy allows, simulate delivery on the SMTP server. Connect, greet, and run a light SMTP check. A polite RCPT TO can verify emails without sending a test email. Expect throttling and temporary blocks, so rate limit carefully and randomize attempts across mail servers.
Be cautious with catch-all setups where the server accepts every recipient. In those cases, even a solid email validator cannot give a hard yes. Blend results from each layer and record reason codes. Done right, these verification checks keep systems fast and accurate without burning goodwill.
Deliverability And Risk Signals You Shouldn’t Ignore
Not every “valid” address is healthy. Some are risky, silent, or hostile to testing. Handle them with intent.
Addresses That Behave Differently
Role accounts like info@ or support@ often filter heavily and rarely match the intended recipient. Watch for temporary email addresses and any disposable email address patterns from niche email providers. Treat these as risky emails and route them to low-stakes sequences first. For freemail, weigh context rather than blocking outright. The goal is accurate results, not false confidence.
Reputation & List Hygiene Signals
Protect your domain from spam traps by vetting sources and confirming purpose. Use lightweight engagement checks as a second pass. Opens and clicks help, but do not prove an email is valid. Track soft bounces and suppress quickly when patterns emerge. Over time, consistent list hygiene keeps your email list responsive and sends strong signals to inbox algorithms. Pair infrastructure checks with behavior data, then update statuses as reality changes. This is how you stay safe, efficient, and welcome in the inbox.
Privacy, Consent, And Compliance—Do It The Right Way
You want validation that respects people and the law. That starts with clear consent and careful handling.
Legal Guardrails You Must Respect
Use an opt-in that fits your risk tolerance. Double opt-in reduces bad data and helps you verify email addresses up front. Single opt-in converts faster but needs stronger downstream checks. Follow core principles in CAN-SPAM, GDPR, and CASL. Tell users why you validate, what you store, and how long you keep it. Honor rights requests quickly.
Ethical Implementation
Explain that validation ensures the email message reaches the right person and that you only keep what helps you deliver. Document what you collect, like domain records, and purge anything not needed to receive emails. Align with email service providers on data flow and retention. Keep logs secure, rotate keys, and review access quarterly. Treat privacy as a feature, not a hurdle.
Build A Lightweight Validation Workflow That Scales
You need a flow that protects reputation without slowing growth. Keep it simple, visible, and consistent.
When To Validate In The Journey
At entry, guide the user with friendly hints. Run server checks for syntax, then confirm the domain and MX. Before first sending, verify the mailbox with a light probe. Over time, re-check aging contacts to confirm valid email addresses still work.
What To Do With Each Result
For valid emails, allow and watch engagement. For riskier outputs like catch-all or roles, slow down and nurture. If a contact is invalid, suppress and invite a fix. Use prompts in-app and in email to correct errors fast.
Operational Safeguards
Batch new records for bulk email verification so you can accurately check at scale. Provide a self-serve path where a user can upload a list and review a results page in a few minutes. Use limits that respect the remote email account and servers. Log reason codes and outcomes. Roll out changes with small cohorts first. Keep the pipeline simple to maintain a clean email list with just a few clicks.
Tools, Libraries, And Automation Without The Headaches
You can build the stack yourself or buy parts. Choose what saves time and keeps control.
DIY Building Blocks
Start with a solid parser and IDN handling. Add DNS resolution and caching. Queue SMTP probes and backoff on errors. A small email checker script plus metrics can cover a lot.
Choosing Vendors Wisely
If you buy, look for an email verification tool that covers syntax, MX, SMTP, roles, and disposable signals. A mature email verification api exposes clear endpoints and an application programming interface that is easy to integrate. Prefer vendors that offer a free account to trial, a user-friendly dashboard, and clear reporting.
Some provide a free email checker for quick lookups. Ask how their email verifiers score risk and how their email verifier decisions map to actions. Review throughput, latency, and how their email verifier work fits your queues. Pick what aligns with your roadmap, not just features.
Troubleshooting Edge Cases You’ll Actually Meet
You will hit cases where a perfect answer is impossible. Be honest and pragmatic.
When “Maybe” Is The Only Honest Answer
On catch-all domains, a server may say every email address exists. Watch engagement and bounces before you promote the contact. Timeouts and 4xx responses happen. Retry with backoff and rotate IPs. Keep retries short to protect reputation.
International And Enterprise Oddities
Quoted strings and plus addressing are valid. Treat them as normal unless policy says otherwise. Some servers block probing. In those cases, weigh domain signals, consent proof, and first-send results from your welcome sequence.
Post-Validation Safeguards
Use soft-bounce thresholds and feedback loops to spot silent traps. Update status as real data arrives. Share patterns with support and sales, so verifying email addresses becomes a team habit. The goal is reliable outreach that protects your business and keeps inboxes welcoming.
Keep Your List Healthy With A Reliable Email Checker
Email verification isn’t just a technical task—it’s how you protect your reputation, budget, and results. Every clean record means one less bounce, one more message reaching the right person. Whether you’re validating a few signups or managing large campaigns, consistent verification keeps your audience real and responsive.
If you’d rather not handle it manually, you can rely on an email checker that quickly confirms syntax, domain, and mailbox accuracy. Our own email verification API does exactly that—giving you dependable results and peace of mind while you focus on what truly matters: sending messages that get delivered. Try our email verification API today!