Email list verification is the safety check your sending reputation deserves. You want clean data, steady inboxing, and fewer headaches. We can get you there with a clear process that fits real teams. Think of the trade show list you imported last week. Or the webinar signups that looked great until bounces spiked.
Good verification filters the junk, protects your domain, and saves the budget you would waste on bad sends. We will break down what gets checked, how tools really work, and when to run them. You will see how to pick a vendor, set fair pricing, and keep data private. We will build a simple workflow, plug it into your ESP, and measure the lift. You will ship confidently, at scale. No guesswork required.
What Email List Verification Really Means
Before we compare tools or prices, let’s get crystal clear on the job to be done and the terms people mix up. You and I need the same language so decisions stay simple.
Cut Through The Jargon: What Exactly Gets Checked
Verification tests each address for basic structure, the domain behind it, and the actual mailbox.
- Syntax Checks: Catches typos and illegal characters.
- Domain and MX Lookups: Confirms the domain exists and can receive mail.
- Mailbox Existence: Uses safe SMTP handshakes to see if a mailbox is real without sending.
- Risk Flags: Identifies traps, disposable services, role accounts, and high-complaint patterns.
These steps turn a messy list into clear, testable outputs you can act on.
Verification vs Validation vs Hygiene
Think in timeframes and scope.
- Verification: One-time screening before a send or import.
- Validation: Ongoing, near real time checks on new signups and changes.
- Hygiene: The broader cleanup. Deduping, suppression syncing, enrichment, and consistent formatting.
You use verification to pass the gate. You use validation and hygiene to keep the house clean.
Risk Labels You Can Act On
Vendors output categories so you can set rules.
- Valid: Safe to send.
- Risky: Catch-all or uncertain. Send with care or warm first.
- Disposable: Block.
- Role-Based: Review by use case.
- Unknown: Park for a second pass or a small test.
Now that we speak the same language, let’s make the business case you can defend.
Why Verification Matters In The Real World
You verify lists to protect your sender reputation and your budget. Here is where the payoffs show up. Think about your last promo. Clean data could have turned a slow start into steady results.
Deliverability You Can See In Your Metrics
Verification tightens the funnel so more emails land where they should.
- Fewer Hard Bounces: Invalid mailboxes get removed before you hit send.
- Fewer Spam Complaints: Risky and disposable addresses do not receive your message.
- Better Inbox Placement: Lower bounce and complaint rates improve domain and IP reputation with mailbox providers.
- More Stable Throughput: Fewer red flags means fewer pauses from your ESP.
You get a cleaner send and healthier performance trends.
Costs You Stop Wasting
Bad addresses drain cash and time. Verification plugs the leaks.
- Lower ESP Fees: You are not paying to send to mailboxes that do not exist.
- Fewer Throttles And Re-sends: Less firefighting after a rough blast.
- Reduced Team Overhead: Fewer support tickets and less list triage.
- Protected Brand: Fewer blocklists and fewer apologies to customers.
Savings show up on invoices and in calmer calendars.
When And How Often To Verify
Use clear triggers and a predictable rhythm.
- New Sources: Events, partner lists, co-registrations.
- List Merges: Acquisitions and CRM deduping projects.
- Event Imports: Trade shows, webinars, and lead magnets.
- Reactivation: Before you message dormant segments.
- Ongoing Cadence: Batch weekly for steady inflow. Real-time at signup for high-risk funnels.
With the why in place, let’s look under the hood so you know how the work really gets done.
How Modern Verification Actually Works Behind The Scenes
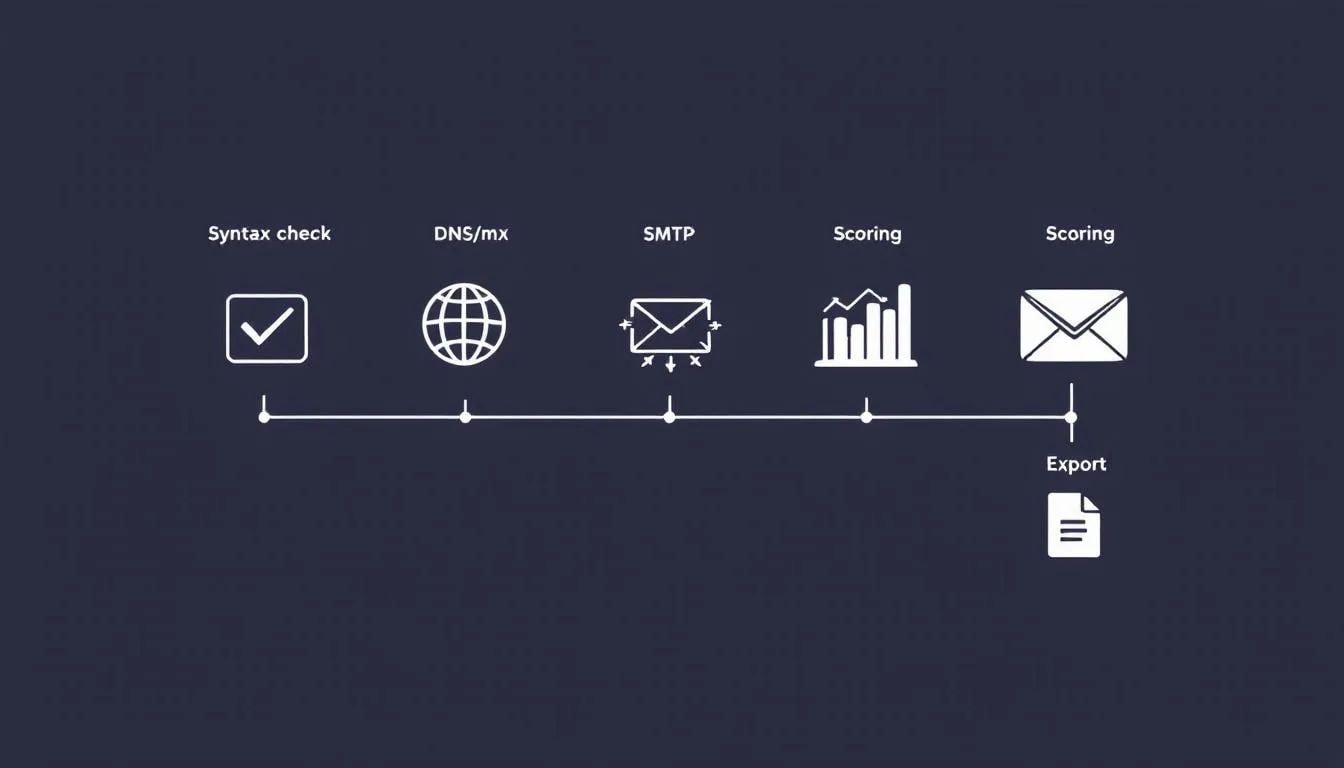
Good vendors follow a predictable, careful process. Knowing it helps you ask smarter questions. It also keeps your tests fair and your outcomes repeatable.
From Upload To Output: How You Can Verify Email Addresses
You start with an upload or an API call. The system ingests your file, tags the source, and normalizes each record. Typos get corrected where safe. Domains are lowercased. Fields are trimmed and standardized.
The engine then runs multi-pass checks. Syntax and DNS first. Mail exchanger lookups next. Finally, mailbox-level tests where possible. Each pass adds signals. The platform scores every address with a clear label and a reason code. You download a clean export that fits your ESP, plus a suppression file for what you should not send.
Keep this simple. Intake. Normalize. Check in layers. Score. Export.
SMTP Checks Done Safely
Mailbox testing should not harm your reputation. A serious vendor manages connection limits, uses warming pools, and respects server responses. Timeouts are conservative. Retries are spaced. Greylisting is handled with patience so you get a real answer without poking the same host again and again.
Ask how they separate verification traffic from marketing sends. Ask how they avoid false positives when a server defers.
Handling The Gray Areas
Catch-all domains return valid for every user. Role accounts invite complaints in some programs but not others. Good systems treat these as risk, not as clean. They use probabilistic scoring, historical patterns, and small live samples when allowed. You set what happens next. Send cautiously. Warm first. Or suppress until you have proof.
You also need to know what data you should share and how to protect it.
Data Privacy And Security You Can Trust
You can verify lists without risking customer trust. Here is the bar to set. Keep it simple. Keep it defensible. Keep it auditable.
Share Only What Is Necessary
Send only what is required to confirm an email address exists. In most cases, that means the address itself and a light source tag from your sign-up forms. Skip names, phone numbers, and other contact details. If your flow supports it, hash addresses before transfer and agree on a format so matches are reliable. Ask for field-level encryption during upload and storage. Limit access to exports inside your team and log every touch.
A lean payload protects customer data and keeps approvals moving. It also prevents accidental exposure of email message history or marketing notes.
Compliance Without The Legalese
Map roles first. You act as the controller. Your vendor is the processor. Put a clear DPA in place. Confirm data residency and cross-border rules with your marketing platforms and email service providers. For GDPR, document lawful basis, retention limits, and erasure steps. For CAN-SPAM, keep consent provenance so each record ties back to its capture date.
Clean records help your email marketing stay compliant while you remove invalid emails and keep valid emails ready for the next campaign.
Security Signals Worth Verifying
Ask for third-party audits such as SOC 2 Type II or ISO 27001. Require encryption in transit and at rest. Review key management and rotation. Define short retention windows and deletion SLAs. Check access controls, SSO, and role-based permissions. Evaluate how the email verifier handles risky emails, duplicate emails, and email syntax errors through an email verifier api or a broader email verification solution. Expect DMARC monitoring alignment and clear reports that turn results into actionable data, so deliverable emails improve and email engagement rises instead of drifting to the spam folder.
With safety covered, let’s choose a partner that will not let you down.
Choosing A Vendor Without Regret
Sales pitches can sound the same. Your questions will not. Use them to separate hype from help. We want a partner that fits your stack, proves results, and stands up when things get busy. Serious email marketers need a vendor that treats email verification as a disciplined workflow, not a feature.
Technology Fit You Can Validate
Start with the engine, not the demo. Ask how the email verification API handles spikes and how the system will verify email addresses at scale without tripping an email server. Check how the platform processes email address syntax and flags invalid addresses before they poison email deliverability. Review concurrency, processing time, and uptime.
Press on handling for catch all emails, spam traps, and list cleaning quality. Confirm whether the stack is true email verification software or a thin wrapper over third-party email verification tools. If you use Google Sheets or a Chrome extension in ops, confirm support.
You should leave with specifics, not adjectives.
Proof Over Promises
Design a pilot that cannot be gamed. Use blind splits across live email campaigns. Track bounce and complaint shifts and report the bounce rate clearly. Validate exports with your ESP and compare to your other deliverability tools.
Ask for real-time verification on new leads and a safe bulk email verification run for backlogs. Inspect reason codes from the mail verifier and confirm accurate outcomes on email validation tests. You want actionable insights, not mystery scoring.
Support You Can Rely On
Great tech still needs humans. Confirm response times, escalation paths, and a clear status page. Review the user interface for clarity and the advanced features you will actually use. Check plan options like pay as you go, monthly subscription, free account, or free plan. Ask about blacklist monitoring and how the email verification service integrates with your marketing stack.
Once the short list is real, you need pricing you can explain to finance.
Pricing And ROI You Can Defend
Cheap is expensive when results slip. Price the full picture, not just the unit cost. A fair deal protects your budget and your reputation at the same time.
Pricing Models And Where Surprises Hide
Start by mapping how you will actually use the service. Then match the plan to your pattern.
- Per email works for unpredictable volumes but can spike on big imports.
- Credit bundles often expire. Confirm the clock and ask about extensions.
- Monthly caps look safe until growth hits the ceiling. Know the throttle rules.
- Overage rates can erase your savings. Get them in writing and test a scenario.
Ask for a sample invoice using your last quarter’s usage so you can see the real math.
Calculate True ROI
Count the savings and the lift, not only the fee. Build a simple model.
- Reduced bounces lower sending costs and protect reputation.
- Better inbox placement improves open and click rates.
- Fewer fire drills save team hours you can redeploy.
- Lower trap and complaint rates reduce the risk of blocklists.
Project the impact on revenue for one or two core programs. Tie it to last year’s numbers to keep the estimate grounded.
Negotiate With Confidence
Good vendors will flex when you are clear about needs.
- Ask for volume tiers that reflect seasonal peaks.
- Request rollover credits to cover slow months.
- Convert pilot spend into contract credits.
- Add exit clauses and clean handoff terms.
- Time renewals away from your busiest season.
Close with a short, clean order form. One page beats ten.
You have the deal. Now let’s turn it into a clean, repeatable workflow.
Your Implementation Blueprint From Raw List To Clean Send
A clear pipeline saves you time and protects your domain. Build it once and reuse it. Keep every step visible so anyone on the team can follow it.
Prep Work That Pays Off
Start with order. Tag every source so you can trace quality later. Dedupe by primary email and a stable contact key. Normalize fields so domains are lowercase and whitespace is trimmed. Create a quarantine bucket for anything that looks off.
Simple checks catch most surprises before they become problems.
- Set file naming rules with dates and source tags.
- Validate column headers so imports never break.
- Hold unknown formats for review, not for sending.
The Verification Pipeline
Move data through clear stages. Ingest to a staging bucket. Run verification in batches sized for your throughput. If a pass times out, send it to automated retries with spacing. Sync suppressions with your ESP before you export new records. Keep versioned exports so you can roll back.
Alert on failures and on unusual spikes in risk. Make logs easy to read. Add a short runbook so support can fix common issues fast.
Decision Rules Everyone Understands
Turn results into actions the team can apply without guessing. Map each risk label to a specific path.
- Valid goes to send.
- Catch-all or uncertain goes to warm with lower volume.
- Role accounts and risky patterns go to nurture or review.
- Invalid and traps go to suppression with a reason code.
Document these rules in your playbook and in your ESP. Audit them monthly and adjust when sources change.
After launch, you prove it worked and keep improving.
Measure What Matters And Close The Loop
Good verification shows up in your numbers. Here is how to track the win. Keep the setup simple so you can repeat it every time.
Core Metrics To Watch
Start with a tight list of indicators. Check them after each send and over rolling windows.
- Hard and soft bounces
- Complaint rate and unsubscribe rate
- Spam trap hits and blocklist checks
- Inbox rate and placement by mailbox provider
- Throughput and deferrals from your ESP
Give each metric a target and a threshold. If a number drifts, pause and investigate before the next send.
Use Controls And Comparisons
You need context to prove impact. Build controls and time windows that show before and after.
- Hold out a small, representative slice that skips verification.
- Compare identical segments across two sends using a seven or fourteen day window.
- Use your ESP diagnostics to confirm changes in throttling, reputation, and placement.
- Track results by source tag so you spot risky partners early.
Document each test so you can reuse it for new lists and new vendors.
Feed Learnings Back Into The System
Close the loop so gains compound. Do not let lessons sit in a slide deck.
- Update scoring rules if a pattern keeps showing up.
- Tighten source intake and form validation where bad data originates.
- Refine suppression logic to stop repeat offenders.
- Share results with sales and events so everyone improves capture quality.
Schedule a quick monthly review. Look at trends, not single sends. Note wins, gaps, and actions for the next sprint.
Avoid the traps that cause most failures, and you will stay ahead.
Myths, Mistakes, And “Too Good To Be True” Offers To Avoid
A few red flags will save you weeks of pain. Keep this list close. When a deal looks magical, slow down and test before you trust.
Free Unlimited Checks And Other Mirages
Real SMTP testing consumes bandwidth, time, and infrastructure. If someone waves a free email banner for everything, ask where the money comes from and how your data is protected. A free email checker is fine for a quick spot test, not for production. The best email verification service will explain costs, limits, and retention in plain language. Clarify whether the vendor shares data with other tools or brokers. Confirm they never store addresses for an email finder or any unrelated upsell.
Pretty Dashboards With Weak Backends
A user-friendly interface helps, but only if the engine can keep up. Stress test the system for latency and concurrency using a small run that mirrors real volume. Check export completeness and file integrity. If the platform claims a bulk email verifier, run a time-boxed batch and compare results to your ESP logs. Ask how the model uses email scoring to label risky records and how those labels support enhancing deliverability and inbox placement to the intended recipient.
Process Gaps That Hurt You
Shortcuts create costly loops later.
- No pilot and no success metrics means no proof.
- Over-reliance on catch-all guesses inflates valid counts.
- Missing consent checks risks spam complaints and blocks.
- No plan for email warmup turns a good list into throttles.
- Treating cold outreach the same as nurtured audiences hides real risk.
- Allowing users to push changes without review undermines controls in your email marketing tools.
Track outcomes and tie them to campaign performance. If a vendor cannot meet these basics, move on.
You are ready to run this with confidence and show results.
Your Next Move — Put Email List Verification To Work
Email list verification is simple when you follow a clear plan. You know what to check, how vendors should work, and when to run it. Start with neat inputs. Verify, score, and route. Use the implementation blueprint to build your pipeline once and reuse it. Map risk labels to actions the team can follow without guessing.
Price the deal on total value, not a teaser rate. Then measure. The metrics section is your daily compass. Track bounces, complaints, traps, placement, and throughput. Use controls so you can prove the lift. Close the loop each month and tweak sources, rules, and suppressions. Put a quarterly review on the calendar. Celebrate wins. Fix the leaks. Keep the flow simple. Your next send will show it in practice. Ready to put this into practice today? Try Verify550’s workflow and see the difference: how an email list validation tool saves the day.